Forensic Detection of Files Deleted via SDelete
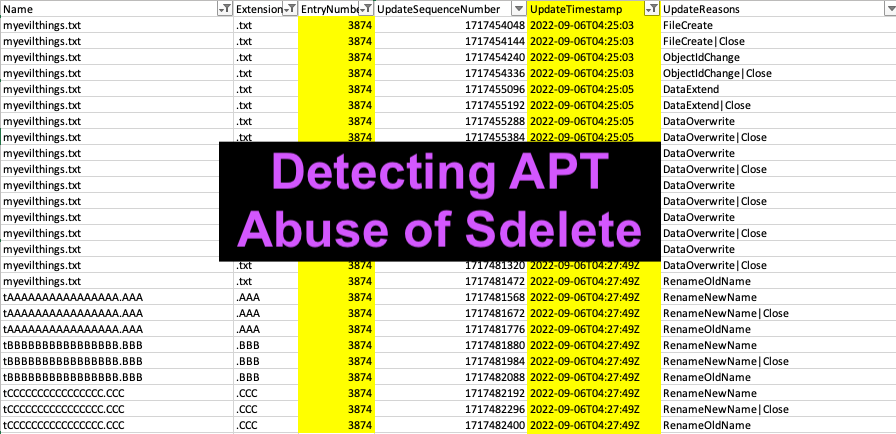
Russian nation-state adversaries abuse the tool “sdelete” to perform file deletion of their attack files. Sdelete is still being used by IRON HEMLOCK (APT29) in 2022 as a part of defence evasion. The tool “sdelete” was created by Mark Russinovich and is used to securely prevent files from being recovered through deleting the file and overwriting the file data in unallocated portions of the disk. What's annoying about this tool is it shows artefacts with overwritten filenames "AAAAAA.AAA" instead of the original name. This is a quick forensics write-up demonstrating that you can in fact, recover the original file names from analysis of $J. DETECTION METHODOLOGY When sdelete is utilised, it leaves obvious traces in the USN Journal, $J file where 26 unique entries will be created in alphabetic order as pictured below. This is a dead giveaway that “sdelete” was utilised by the threat actors. The best way to review the $J file is to parse by the Entry Number. This correspon...