Detecting Linux Anti-Forensics Log Tampering
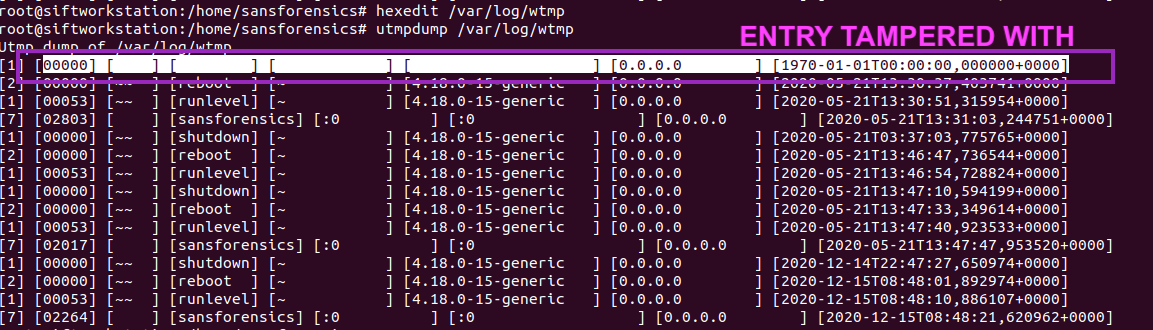
When forensically examining Linux systems for malicious intrusion, responders often rely on the following three artefacts to determine logins and logouts: /var/run/utmp – currently logged in users /var/run/wtmp – current, past logins and system reboot /var/log/btmp – bad login attempts Of course, these artefacts are not all you can forensically investigate for malicious access (there are other artefacts you can examine), however, these will be the focus of this anti-forensics blog post. In this post, I will walk through two methods of removing and tampering with these aretfacts to delete the malicious logins you want to hide. The first method removes the log line completely from the file through overwriting the binary file, the second method focuses on altering the hex of the file but is more obvious to detect. I will then walk through a simple way of detecting both methods based on timestamps that you can check. If timestamps are king – then I’ll be his queen! ...

