Hunting for APT Abuse of Exchange
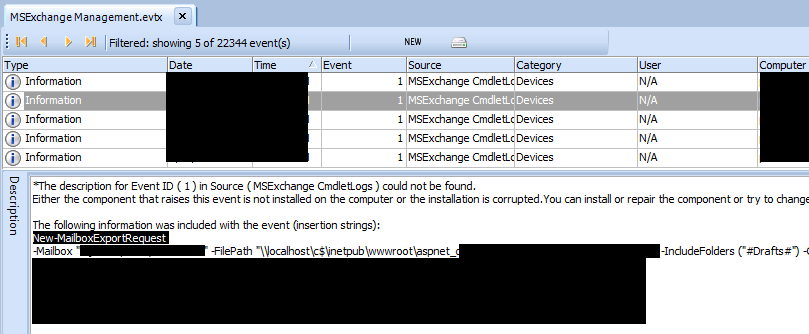
APT abuse of Exchange is not a new topic, but I noticed there weren’t enough write-ups of hunting methodologies, so I decided to write one based on the various attack techniques I’ve seen various APTs use over the last 2 years. This is not a comprehensive guide as there honestly is WAY too much for me to write and cover (I don’t have enough time T_T but will add to this post over time). I’m going to show you specifically some key areas you can focus on when hunting for malicious behaviour. This guide will not cover the entire attack map of what happens in an APT case where Exchange is abused, it will only cover key areas to hunt on Exchange. Over the course of the last few years there has been a heavy abuse of legacy authentication from APT groups from various nations, with a strong focus especially on EWS and other legacy auth methods as their preferred method of access. If there is a business need for legacy authentication… (aka you still have legacy authentication enabled) then
