Detecting Fake Events in Azure Sign-in Logs
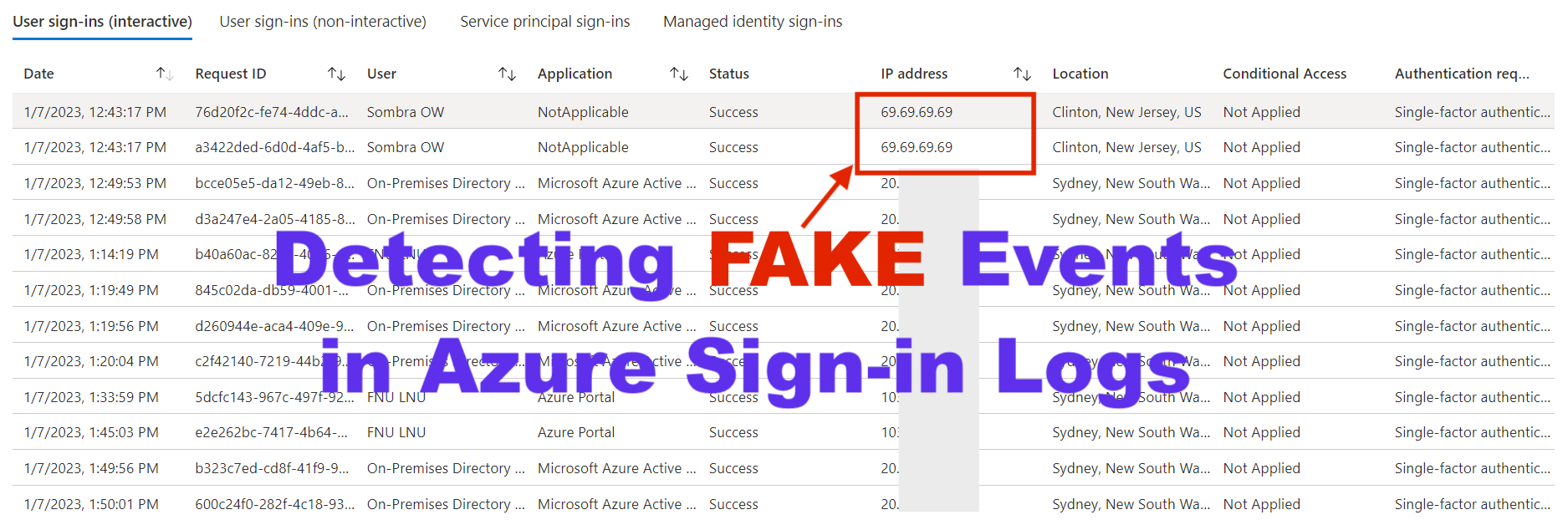
Threat actors can create and populate fake logs in the Azure sign-in logs that look like legitimate events The parameters they can spoof in the logs include (and are not limited to): Timestamp of when the events are generated User account IP addresses Network location type During forensic investigations, analysts may not be aware that some of the logs are not “legitimate” and start recording indicators of compromise that are not necessarily “real”. Further, this raises the question of “trust” regarding log sources – highlighting that during forensic investigations, it’s always best practice to utilise multiple sources rather than solely relying on one source. This technique has previously been written about by @DrAzureAD in his blog post here and was also covered by Secureworks Counter Threat Unit here . As per @DrAzureAD’s blog, this attack can be conducted TWO ways; the second method being harder to detect than the first: Method 1: An attacker gains local admin / domain ad...