Azure Command Line Forensics - Host Based Artifacts
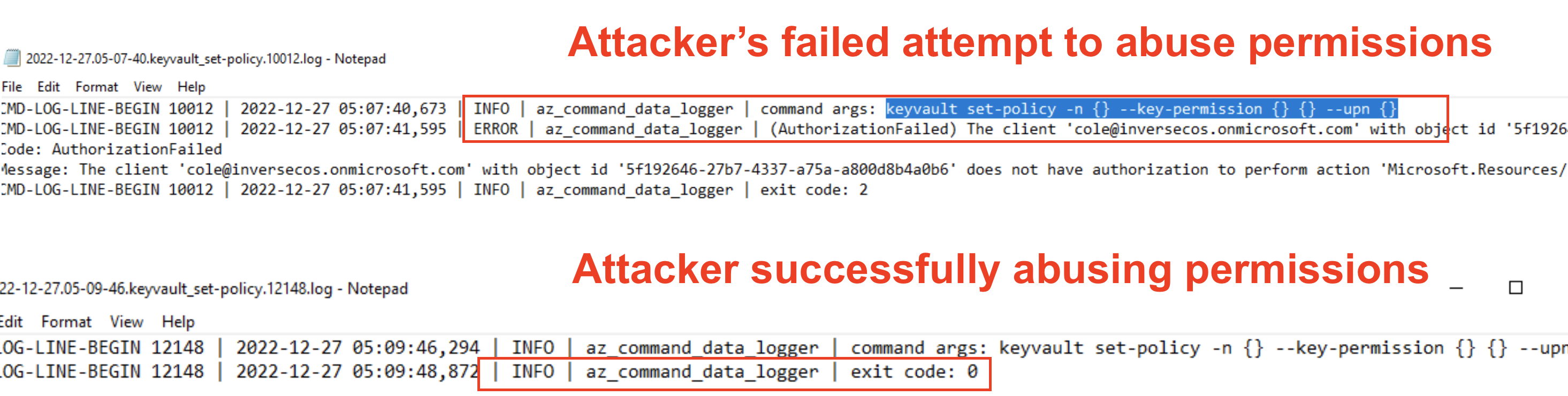
On most of the on-premises to cloud lateral movement compromises I’ve worked relating to Azure, threat actors typically leverage a bunch of different command-line focused tools. They use these tools to perform enumeration of the victim’s Azure environment, backdooring active directory, various persistence techniques and lateral movement. These are generally a combination or one of the following (this is not a comprehensive list... just examples): AADInternals Azure CLI AzureAD PowerShell Threat actors run these tools on servers and hosts of interest i.e. AD FS servers, AD CS servers to abuse pass-through authentication or abuse identity federation. The Azure CLI has also been leveraged by attackers to perform various enumeration / reconnaissance style attacks. If you want more detailed information around how to detect and perform attacks against Azure and Microsoft 365, check out my " Attacking and Defending Azure / M365 " course. High-Level Methodology First to perform t...