How to Detect Malicious OAuth Device Code Phishing
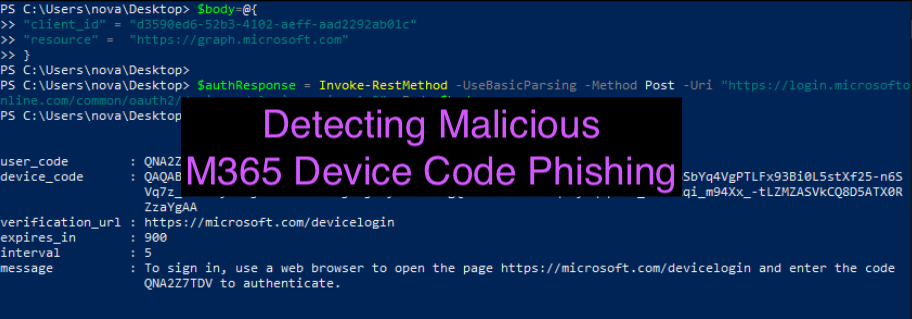
In this brilliant blog ( https://aadinternals.com/post/phishing/ ) by @DrAzureAD, he introduced a method of phishing M365 accounts that threat actors can leverage by abusing device code authentication. There have been a lot of great blogs citing this technique but not much written about the detection… which is why I am here 🙂 The reason I am writing about this technique is that it’s significantly more difficult to detect than OAuth abuse for malicious application registrations. The reason for this is, the entire premise of the phish occurs within the microsoftonline.com namespace and does not redirect the user to any third-party website and there is no need for any 3rd party application authorization/registration. This method of phishing also bypasses MFA requirements as the attacker gains access to the user’s refresh and access token. I wanted to revisit this technique and blog about a detection for this type of attack. As usual, I’ve broken this blog post into two sections: At...